VPC Route Table
Your VPC has an implicit router, and you use route tables to control where network traffic is directed.
Each subnet in your VPC must be associated with a routing table, which controls the routing for the subnet (subnet route table).
You can explicitly associate a subnet with a particular route table. Otherwise, the subnet is implicitly associated with the main route table.
A subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same route table.
Key Concepts
1) Main route table
The route table that automatically comes with your VPC.
It controls the routing for all subnets that are not explicitly associated with any other route table.
2) Custom route table
- A route table that you create for your VPC.
3) Route table association
- A key mechanism for controlling how network traffic flows within your VPC, ensuring that it is directed correctly between subnets, internet gateways, and other network resources like VGW, NAT Gateways, Internet Gateways.
4) Subnet route table
- A route table that's associated with a subnet.
5) Destination
The destination is the "where" of the network traffic, specifying the destination IP address or range of addresses.
For example, an external corporate network with a 172.16.0.0/12 CIDR.
6) Target
- The target is the "through which" part, indicating the gateway, network interface, or connection that should be used to reach that destination.
7) Local route
- A default route for communication within the VPC.
Internet Gateway
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between your VPC and the internet.
An internet gateway serves two purposes:
To provide a target in your VPC route tables for internet-routable traffic.
To perform network address translation (NAT) for instances that have been assigned public IPv4 addresses.
Key Points
Public Subnet: If a subnet is associated with a route table that has a route to an internet gateway, it's known as a public subnet.
Private Subnet: If a subnet is associated with a route table that does not have a route to an internet gateway, it's known as a private subnet.
By specifying a route for
0.0.0.0/0(IPv4) or::/0(IPv6), we direct all traffic with destinations outside the VPC to the internet gateway. This means any traffic from instances in the public subnet going to destinations beyond the VPC will be routed to the internet.Alternatively, we can define more specific routes to restrict internet access to certain IP ranges. For example, if your company has specific public IP addresses for its services outside of AWS, you can create routes for these addresses. This approach provides more control over which destinations can be accessed over the internet from your public subnet.
Network ACL
- A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets. You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
Network ACL Rule Components
Rule number: Rules are evaluated starting with the lowest numbered rule. As soon as a rule matches traffic, it's applied regardless of any higher-numbered rule that might contradict it.
Type: The type of traffic; for example, SSH. You can also specify all traffic or a custom range.
Protocol: You can specify any protocol that has a standard protocol number.
Port range: The listening port or port range for the traffic. For example, 80 for HTTP traffic.
Source: The source of the traffic (CIDR range).
Destination. The destination for the traffic (CIDR range).
Allow/Deny: Whether to allow or deny the specified traffic.
Key Points
VPC automatically comes with a modifiable default network ACL. By default, it allows all inbound and outbound IPv4 traffic and, if applicable, IPv6 traffic.
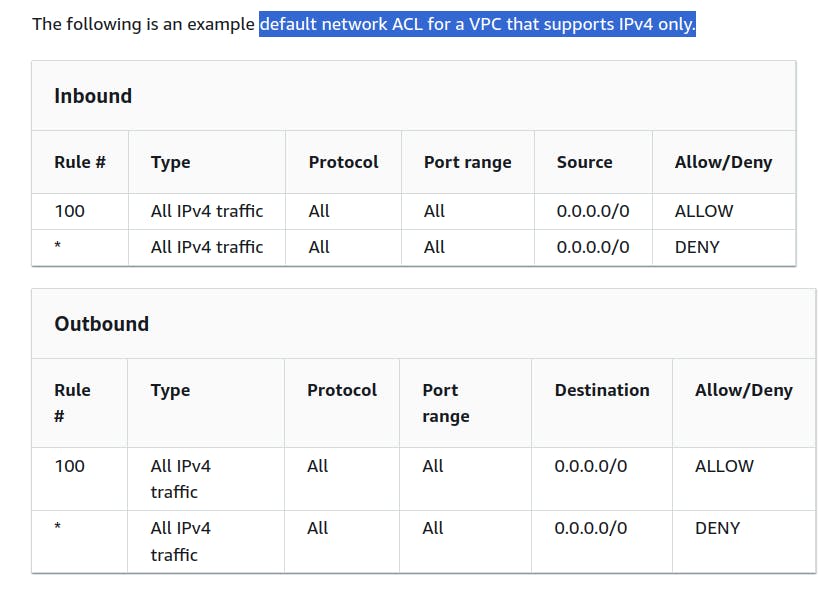
We can create a custom network ACL and associate it with a subnet. By default, each custom network ACL denies all inbound and outbound traffic until you add rules.
Each subnet in your VPC must be associated with a network ACL. If we don't explicitly associate a subnet with a network ACL, the subnet is automatically associated with the default network ACL.
We can associate a network ACL with multiple subnets. However, a subnet can be associated with only one network ACL at a time. When we associate a network ACL with a subnet, the previous association is removed.
A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic.
Network ACLs are stateless, which means that responses to allowed inbound traffic are subject to the rules for outbound traffic (and vice versa).
A network ACL contains a numbered list of rules. NACL evaluate the rules in order, starting with the lowest numbered rule, to determine whether traffic is allowed in or out of any subnet associated with the network ACL. The highest number that we can use for a rule is 32766. It is recommended that we should start by creating rules in increments (for example, increments of 10 or 100) so that you can insert new rules where you need to later on.
Default NACL
Custom NACL
Security Group
- A security group acts as a virtual firewall for your instance to control inbound and outbound traffic.
- When you launch an instance in a VPC, you can assign up to five security groups to the instance.
- Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC can be assigned to a different set of security groups.
Key Points
We can specify allow rules, but not deny rules. We can specify separate rules for inbound and outbound traffic.
Security group rules enable you to filter traffic based on protocols and port numbers.
Security groups are stateful — if we send a request from our instance, the response traffic for that request is allowed to flow in regardless of inbound security group rules. Responses to allowed inbound traffic are allowed to flow out, regardless of outbound rules.
Each VPC automatically comes with a default security group. If we don't specify a different security group when you launch the instance, the default security group gets associated with your instance.
Default Security Group: