AWS Networking helps the user to isolate the cloud infrastructure.
It also helps to scale the request handling capacity and connect the physical and private virtual network.

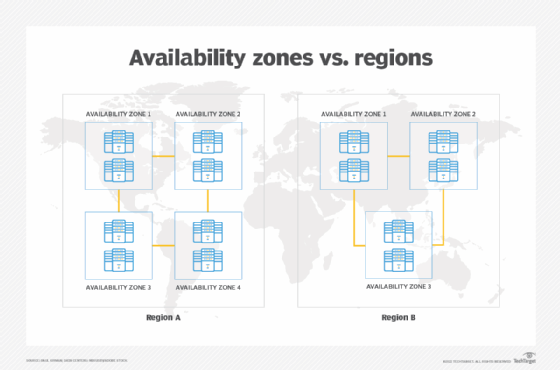
What is Region & Availability Zones?
AWS has the concept of a Region, which is a physical location around the world where they cluster data centers.
They call each group of logical data centers an Availability Zone.
Each AWS Region consists of multiple, isolated, and physically separate AZs within a geographic area.
What is Edge Locations?
- Edge locations are part of the AWS global network infrastructure and are used by Amazon CloudFront, the content delivery network (CDN) service, to cache copies of your content closer to your end-users, reducing latency and improving the performance of delivering content to them.
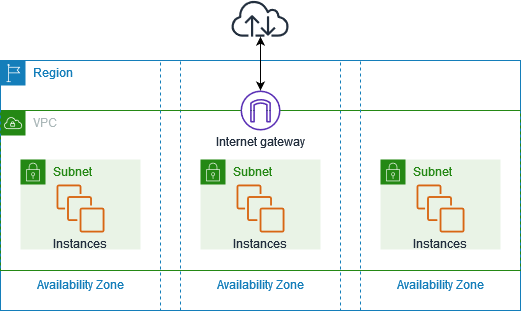
Amazon Virtual Private Cloud (VPC)
Build on a logically isolated virtual network in the AWS cloud
Amazon Virtual Private Cloud (Amazon VPC) is a service that lets you launch AWS resources in a logically isolated virtual network that you define.
You have complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
You can use both IPv4 and IPv6 for most resources in your virtual private cloud, helping to ensure secure and easy access to resources and applications.
AWS VPC Benefits
a) Reachability Analyzer
Reachability Analyzer is a static configuration analysis tool that enables you to analyze and debug network reachability between two resources in your VPC.
After you specify the source and destination resources in your VPC, Reachability Analyzer produces hop-by-hop details of the virtual path between them when they are reachable, and identifies the blocking component when they are unreachable.
b) VPC Flow Logs
You can monitor your VPC flow logs delivered to Amazon S3 or Amazon CloudWatch to gain operational visibility into your network dependencies and traffic patterns, detect anomalies and prevent data leakage, or troubleshoot network connectivity and configuration issues.
The enriched metadata in flow logs helps you gain additional insights into who initiated your TCP connections and the actual packet-level source and destination for traffic flowing through intermediate layers such as the NAT Gateway.
You can also archive your flow logs to assist in meeting certain compliance requirements.
c) VPC Traffic Mirroring
VPC traffic mirroring allows you to copy network traffic from an elastic network interface of Amazon EC2 instances and then send the traffic to out-of-band security and monitoring appliances for deep packet inspection.
With VPC traffic mirroring, you can detect network and security anomalies, gain operational insights, implement compliance and security controls, and troubleshoot issues.
VPC Traffic Mirroring as a feature that gives you direct access to the network packets flowing through your VPC.
d) Ingress Routing
Ingress routing in AWS involves directing incoming network traffic from external sources to resources within a Virtual Private Cloud (VPC) or network environment.
It is typically managed through the configuration of route tables, network access control lists (NACLs), and security groups.
e) Security Groups
Security groups act as a firewall for associated Amazon EC2 instances, controlling both inbound and outbound traffic at the instance level.
When you launch an instance, you can associate it with one or more security groups that you've created. Each instance in your VPC could belong to a different set of security groups.
If you don't specify a security group when you launch an instance, the instance is automatically associated with the default security group for the VPC.
f) Network Access Control List
A network access control list (NACLs) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
You might set up network ACLs with rules similar to your security groups in order to add an additional layer of security to your VPC.
AWS VPC Components
a) Virtual private cloud (VPC)
- A virtual network dedicated to your AWS account.
b) Subnet
A range of IP addresses in your VPC. It is a portion of the network that shares a common address component.
All devices whose addresses have the same prefix are in the same subnet. For example, all those devices whose IP address would start with 172.31.1 would be part of the same subnet.
There are two types of subnets. Private Subnet where resources are not exposed to the outside world and Public Subnet where resources are exposed to the internet through Internet Gateway.
c) Route table
A set of rules, called routes, that are used to determine where network traffic is directed.
Route table specifies the destination (IP address) and target (where do want to send the traffic of that destination).
The target can be Internet gateway, NAT gateway, Virtual private gateway, VPC peering connection, etc
d) Internet gateway
- A gateway that you attach to your VPC to enable communication between resources in your VPC and the internet.
e) VPC endpoint
Enables you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection.
Instances in your VPC do not require public IP addresses to communicate with resources in the service. Traffic between your VPC and the other service does not leave the Amazon network.
f) CIDR block
CIDR stands for Classless Inter-Domain Routing. It is a method used to specify a range of IP addresses.
In CIDR notation, an IP address is followed by a slash ("/") and a number, which represents the number of bits in the subnet mask.
For example, "192.168.1.0/24" represents the IP address "192.168.1.0" with a subnet mask of 255.255.255.0, indicating that the range includes all IP addresses from 192.168.1.0 to 192.168.1.255.
g) NAT Gateway
NAT Gateway is used to allow instances in a private subnet to initiate outbound traffic to the internet, while preventing inbound traffic from reaching those instances. It is commonly used for instances that require internet access but do not need to be directly reachable from the internet.
NAT Gateway resides in the public subnet of an Availability Zone, as it requires a route to the internet. It does not update the route table of the private subnet; instead, the route table of the private subnet is updated to send outbound traffic to the NAT Gateway.
An Elastic IP (EIP) must be attached to the NAT Gateway when creating it. This EIP allows the NAT Gateway to have a static public IP address for outbound traffic.
NAT Gateway supports TCP, UDP, and ICMP protocols for outbound traffic.
h) Elastic IP
It is a static IP address that never changes and is a reserved public IP address that can be assigned to any Instance in a particular region.
An elastic IP is reserved for your AWS account and is yours until you release it.
With an EIP, you can mask the failure of an instance or software by rapidly remapping the address to another instance in your account.
i) Security Groups
Security Groups (SGs) act as virtual firewalls for your Amazon Elastic Compute Cloud (Amazon EC2) instances to control inbound and outbound traffic.
When you launch an instance, you can assign one or more security groups to it.
SGs control the inbound and outbound traffic for your instances. You can specify the protocols, ports, and IP address ranges that are allowed to reach your instances.
Security Groups are stateful, which means if you allow inbound traffic for a specific port, the corresponding outbound traffic for that port is automatically allowed, regardless of the outbound rules you've defined.
By default, all inbound traffic is blocked, and all outbound traffic is allowed. You must explicitly define rules to allow inbound traffic.
Security Groups are associated with individual instances, not subnets. This allows you to have different security configurations for different instances within the same subnet.
You can modify the rules of a security group at any time. The new rules are automatically applied to all instances associated with the security group.
j) Network Access Control Lists (NACL)
NACLs act as a firewall at the subnet level, allowing you to control inbound and outbound traffic to and from instances in the subnet.
Unlike security groups, which are stateful, NACLs are stateless. This means that you must define both inbound and outbound rules for each desired flow of traffic. For example, if you allow inbound traffic on port 80 (HTTP), you must also explicitly allow outbound traffic on port 80 for the response.
NACLs are evaluated based on numbered rules in sequential order, starting with the lowest number. Once a rule matches a packet, no further rules are evaluated for that packet. This differs from security groups, where all rules are evaluated, and the most permissive rule applies.
Each subnet in a VPC is associated with a default NACL, which allows all inbound and outbound traffic by default. You can create custom NACLs and associate them with subnets to restrict or allow specific types of traffic.
k) VPC Peering
A VPC peering connection allows you to route traffic between two Virtual Private Cloud’s using IPv4 or IPv6 private addresses.
Instances in either VPC can communicate with each other as if they are within the same network.
You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account.
VPC peering allows you to connect two VPCs privately using private IP addresses, without the need to traverse the public internet.
VPC peering can be established between VPCs in different AWS regions, allowing for inter-region communication using private IP addresses.
l) Virtual Private Gateway
A Virtual Private Gateway (VGW) is a component of Amazon Virtual Private Cloud (VPC) used for connecting your VPC to on-premises networks and other AWS services over VPN or Direct Connect.
VGWs use Border Gateway Protocol (BGP) to automatically update the routing tables for your VPC, ensuring that traffic is routed correctly between your VPC and other networks.
There is no additional charge for using a VGW within an AWS region. However, standard data transfer charges apply for data transferred over the VPN connection.
m) Customer Gateway
A Customer Gateway is used to establish an encrypted VPN connection between your on-premises network and your Amazon VPC. This allows you to securely extend your on-premises network into the AWS cloud.
Customer Gateways can be hardware-based, such as routers or VPN appliances, or software-based, such as a VPN client running on a virtualized server. They must be compatible with the Internet Key Exchange (IKE) protocol used by AWS.
Once the VPN connection is established, traffic between your on-premises network and your VPC is routed through the Customer Gateway. You can use static routes or dynamic routing protocols, such as BGP, to manage the routing of traffic.
There is no additional charge for using a Customer Gateway. However, standard data transfer charges apply for data transferred over the VPN connection.
n) Network Interface
A network interface in AWS is a virtual network interface card (VNIC) that you can attach to an instance in a Virtual Private Cloud (VPC). It allows the instance to communicate with other instances in the same VPC, other VPCs, and the internet.
Each instance in AWS has a primary network interface that is created when the instance is launched. You can also attach additional network interfaces, known as secondary interfaces, to an instance to enable additional networking capabilities.
The primary and secondary network interfaces in AWS are implemented using Elastic Network Interfaces (ENIs). An ENI has attributes such as a MAC address, private IP address, and security groups that control inbound and outbound traffic.
You can attach and detach network interfaces from instances. When you attach a network interface to an instance, it becomes available to the operating system of the instance as a network interface.
Network interfaces are commonly used for scenarios such as creating a multi-homed instance with multiple private IP addresses, creating a management network separate from the primary network, or enabling network traffic mirroring for monitoring and security analysis.
