Table of contents
A computer network is the group of interconnected computers connected together to share files and exchange data.
Each device on network can be called as nodes or clients and they are identified by unique address called IP address to communicate with each other.
Types of Networking
a) Personal Area Network (PAN)
Smallest network that is very personal to a user.
Purpose is to allow communication between the devices without being necessarily connected to the internet.
Can be wired/wireless.
Eg. Bluetooth Remote Controller
b) Local Area Network (LAN)
A computer network spanned inside a building and operated under a single administrative system is generally referred as LAN.
Most often within the same building.
c) Wireless Local Area Network (WLAN)
Just like LAN but wireless.
d) Campus Area Network (CAN)
Larger than LAN but smaller than MAN.
e) Enterprise Private Network (EPN)
An Enterprise Private Network (EPN) is a secure network infrastructure that is used exclusively by an organization. It is designed to connect various locations, such as offices, data centers, and remote workers, in a way that ensures security, reliability, and performance.
f) Metropolitan Area Network (MAN)
Larger than LAN smaller than WAN.
Spans an entire geographic area such as typically a town or a city.
g) Wide Area Network (WAN)
Internet is the basic example of WAN.
h) Storage Area Network (SAN)
It's a specialized high-speed network that connects servers and storage devices, such as disk arrays and tape libraries, to provide block-level storage access.
SANs are typically used to enhance storage devices' accessibility and performance, allowing them to appear as locally attached to the operating system.
Specifically designed to connect storage devices.
i) System Area Network (SAN)
A high-performance network that connects computers and other devices, such as storage systems and peripherals, at the system level.
Designed to connect multiple systems together to achieve high-speed communication and data transfer.
Often used in high-performance computing (HPC) environments, such as supercomputing clusters, where low latency and high bandwidth are critical.
j) Passive Optical Local Area Network (POLAN)
A type of local area network that uses optical fibers and passive optical components to provide connectivity between end devices. Unlike traditional Ethernet LANs, which use copper cables and active networking equipment like switches, POLANs leverage the passive nature of optical fibers to create a network that is cost-effective, energy-efficient, and easy to maintain.
POLAN is called passive because it primarily relies on passive optical components, such as splitters and connectors, to distribute optical signals within the network. Unlike active components like switches or routers, which require power to operate and manage data traffic, passive components do not require power and simply transmit signals without any processing or amplification.
Point-to-Multipoint Topology: POLANs typically use a point-to-multipoint topology, where a single optical fiber serves multiple end devices.
k) Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a technology that allows you to create a secure connection to another network over the Internet.
It can be used to access resources on a network as if you were physically there. VPNs are commonly used by businesses to provide remote access to their internal networks for employees working from home or traveling.
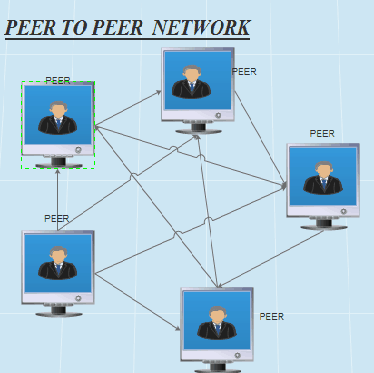
l) Peer-to-peer (P2P) networks
P2P networks connect individual computers directly to each other, rather than through a centralized server.
OSI Model
The open systems interconnection (OSI) model is a conceptual model created by the International Organization for Standardization which enables diverse communication systems to communicate using standard protocols. In plain English, the OSI provides a standard for different computer systems to be able to communicate with each other.
The OSI Model can be seen as a universal language for computer networking.
It’s based on the concept of splitting up a communication system into seven abstract layers, each one stacked upon the last.
Different OSI Layers Explored
a) Layer-7: Application Layer
Human-Computer interaction layer, where application can access network services.
Few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), Post Office Protocol (POP), Simple Mail Transfer Protocol (SMTP), and Domain Name System (DNS).
b) Layer-6: Presentation Layer
Ensure that data is in use-able format, also this is where encryption happens.
A good example of this is encryption and decryption of data for secure transmission - this happens at Layer 6.
c) Layer-5: Session Layer
Maintain Session and is responsible for controlling ports and sessions.
Functions at this layer involve setup, coordination (how long should a system wait for a response, for example) and termination between the applications at each end of the session.
d) Layer-4: Transport Layer
Transmits data using transmission protocol such as TCP, UDP.
The best known example of the Transport Layer is the Transmission Control Protocol (TCP), which is built on top of the Internet Protocol (IP), commonly known as TCP/IP.
TCP and UDP port numbers work at Layer 4, while IP addresses work at Layer 3, the Network Layer.
e) Layer-3: Network Layer
Decides which physical path data will take.
In its most basic sense, this layer is responsible for packet forwarding, including routing through different routers
f) Layer-2: Data Link Layer
Defines format of the data on the network.
It’s in charge of data encapsulation under the form of packets and their interpretation at the physical layer.
g) Layer-1: Physical Layer
Transmit raw bit stream over the physical medium.
This can include everything from the cable type, radio frequency link (as in an 802.11 wireless systems), as well as the layout of pins, voltages and other physical requirements.
TCP/IP Model
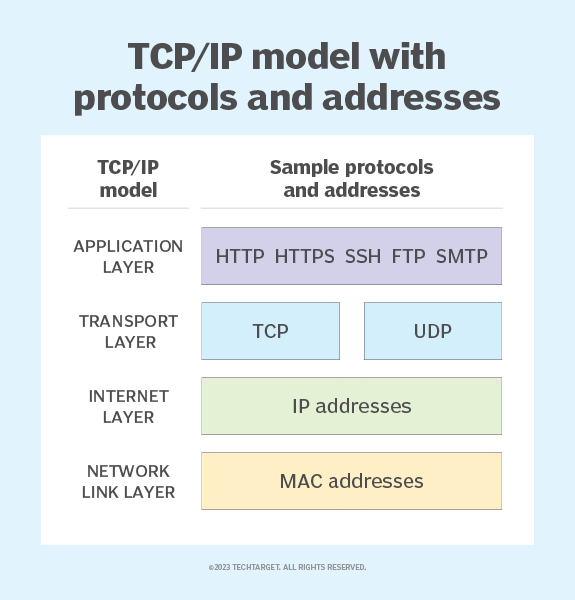
Internet uses TCP/IP protocol suite, also known as Internet suite. This defines Internet Model which contains four layered architecture.
OSI Model is general communication model but Internet Model is what the internet uses for all its communication.
The internet is independent of its underlying network architecture so is its Model.
This model has the following layers:
a) Application Layer:
This layer defines the protocol which enables user to interact with the network.
For example, FTP, HTTP etc.
b) Transport Layer:
This layer defines how data should flow between hosts.
Major protocol at this layer is Transmission Control Protocol (TCP). This layer ensures data delivered between hosts is in-order and is responsible for end-to-end delivery.
c) Internet Layer:
Internet Protocol (IP) works on this layer.
This layer facilitates host addressing and recognition. This layer defines routing.
d) Network Link Layer:
- Provides the same functionality as the physical, the data link and network layers in the OSI model.
OSI Model Vs TCP/IP Model
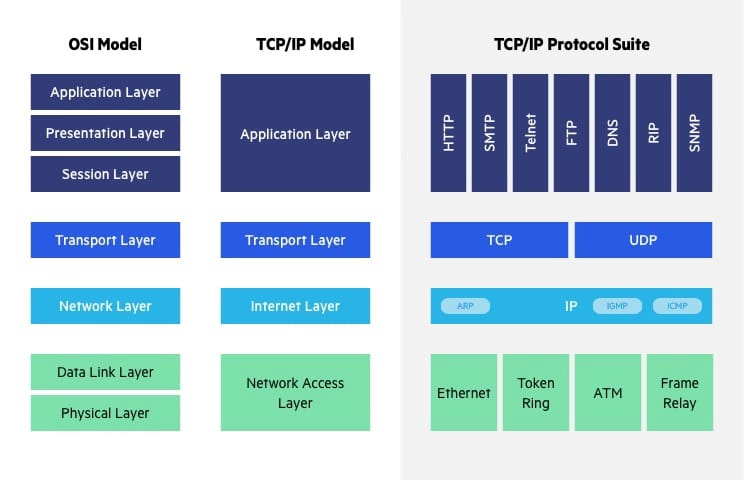
OSI Model:
Conceptual framework: OSI is a theoretical model that describes how network communication should ideally occur. It defines seven layers that standardize network communication functions.
Protocol-independent: The OSI model doesn't specify any particular protocols. It focuses on the services provided at each layer.
Less common use: While a valuable teaching tool, the OSI model isn't widely used in actual network implementations due to its complexity.
TCP/IP:
Practical implementation: TCP/IP is a suite of communication protocols that forms the basis for the internet. Devices use TCP/IP protocols to connect and exchange data.
Protocol-dependent: TCP/IP defines specific protocols for each layer.
Widely used: TCP/IP is the dominant protocol suite for internet communication.
Network Protocols
What is Network Protocol?
In networking, a protocol is a standardized way of doing certain actions and formatting data so that two or more devices are able to communicate with and understand each other.
It define the rules that govern the communications between two computers connected to the network.
Functions
- Addressing and routing of messages, error detection and recovery, sequence and flow controls etc.
Protocol Vs Protocol Specifications
- While the term "protocol" is used to refer to the general rules and conventions of communication, "protocol specifications" refer to the detailed technical documentation that defines how these rules are implemented in practice.
Commonly Used Protocols:
a) Transmission Control Protocol (TCP)
Key features of TCP include:
Connection-Oriented Communication: TCP establishes a connection between two devices before data is exchanged. This connection is maintained until all data has been exchanged, after which it is terminated.
Reliable Data Delivery: TCP ensures that data is delivered reliably to the destination. It uses acknowledgments and re-transmissions to guarantee that data is received correctly, even if packets are lost or corrupted during transmission.
Ordered Data Delivery: TCP ensures that data is delivered to the destination in the same order in which it was sent. This is important for applications that require data to be processed in a specific sequence.
Flow Control: TCP implements flow control mechanisms to prevent a fast sender from overwhelming a slow receiver. It uses sliding window protocols to control the amount of data sent before receiving acknowledgment.
Congestion Control: TCP includes congestion control mechanisms to prevent network congestion and ensure fair sharing of network resources among users.
Full-Duplex Communication: TCP supports full-duplex communication, allowing data to be sent and received simultaneously between two devices.
b) Internet Protocol (IP)
Key features of the Internet Protocol include:
Addressing: IP addresses are used to uniquely identify devices on a network. IPv4 addresses are 32-bit addresses, typically represented in dotted-decimal notation (e.g., 192.168.1.1), while IPv6 addresses are 128 bits in length and are represented in hexadecimal notation (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
Packet Routing: IP determines the best path for data packets to travel from the source to the destination across interconnected networks. Routers use IP routing tables to make forwarding decisions based on the destination IP address of each packet.
Packet Fragmentation and Reassembly: IP can fragment large packets into smaller packets for transmission across networks with smaller maximum transmission units (MTUs). At the destination, IP reassembles the fragmented packets into the original large packet.
Best Effort Delivery: IP operates on a best-effort delivery basis, meaning that it does not guarantee packet delivery or provide mechanisms for error recovery. Higher-layer protocols, such as TCP, are responsible for reliable data delivery.
Versioning: There are two main versions of the Internet Protocol in use today: IPv4 and IPv6. IPv4 is the older and more widely used version, but IPv6 is gradually replacing it due to IPv4 address exhaustion and the need for more addresses.
c) User Datagram Protocol (UDP)
Key features of UDP include:
Connectionless: UDP does not establish a connection before sending data. Each packet is sent independently, and the receiver does not send acknowledgments back to the sender.
Unreliable: UDP does not guarantee delivery of packets. Packets may be lost, duplicated, or delivered out of order. It is up to the application layer to handle any reliability issues if needed.
Low Overhead: UDP has lower overhead compared to TCP because it does not require the establishment and maintenance of a connection, nor does it perform error checking and re-transmission of lost packets.
No Flow Control: UDP does not provide flow control mechanisms to prevent a sender from overwhelming a receiver with data. It is the responsibility of the application to manage data flow if needed.
Usage: UDP is commonly used in applications where low latency and high-speed transmission are more important than reliability, such as real-time multimedia streaming, online gaming, DNS (Domain Name System) queries, and Voice over IP (VoIP) communications.
d) Post Office Protocol (POP)
POP3 (Post Office Protocol version 3): POP3 is a protocol used by email clients to retrieve email messages from a mail server over a TCP/IP connection. It is the most widely used version of the Post Office Protocol.
POP2 (Post Office Protocol version 2): POP2 is an older and less commonly used version of the Post Office Protocol. It has largely been replaced by POP3.
The main difference between POP3 and other email protocols like IMAP (Internet Message Access Protocol) is that POP3 typically downloads emails to your device and removes them from the server, while IMAP keeps the emails on the server and syncs them with your device.
e) Internet Message Access Protocol (IMAP)
IMAP (Internet Message Access Protocol) and IMAP4 (Internet Message Access Protocol version 4) refer to the same protocol. IMAP4 is the latest version of the IMAP protocol and is widely used for retrieving email messages from a mail server and managing them on the server.
IMAP4 includes several improvements and enhancements over earlier versions of the protocol. Some key features of IMAP4 include:
Message Flags: IMAP4 supports flags that can be used to mark messages as read, unread, flagged, or deleted. These flags are stored on the server and can be synchronized between multiple email clients.
Folder Management: IMAP4 allows users to create, rename, and delete folders on the mail server. This provides a way to organize email messages into different folders for easier management.
Selective Download: IMAP4 allows email clients to download only the headers of messages, which include information such as the sender, subject, and date. The full content of the message is downloaded only when the user opens the message.
Offline Access: Some email clients support offline access with IMAP4, allowing users to access their email messages even when they are not connected to the internet. Changes made offline are synced with the server once a connection is re-established.
Security: IMAP4 supports encryption using protocols like TLS (Transport Layer Security) to secure the transmission of email messages between the client and the server.
POP or IMAP?
In general, IMAP is more flexible and suitable for most users, especially those who use multiple devices to access their emails. However, if you prefer to store emails locally and don't need access from multiple devices, POP may be a more suitable choice.
f) File Transfer Protocol (FTP)
FTP (File Transfer Protocol) is a standard network protocol used to transfer files between a client and a server on a computer network. FTP is often used to upload and download files from a web server, making it a common tool for website maintenance and file sharing.
Key features of FTP include:
Two-Connection Model: FTP uses two separate connections for file transfer: a control connection and a data connection. The control connection is used to send commands and receive responses, while the data connection is used to transfer files.
Authentication: FTP supports various authentication methods, including username and password, to verify the identity of users accessing the server.
Passive and Active Mode: FTP can operate in passive or active mode for data transfer. In active mode, the server initiates the data connection to the client, while in passive mode, the client initiates the data connection to the server. Passive mode is often used in situations where the client is behind a firewall or NAT.
Directory Listing: FTP allows clients to list the contents of directories on the server, making it easy to navigate and manage files.
Security: FTP does not encrypt data transferred between the client and server, making it susceptible to eavesdropping. However, FTPS (FTP Secure) and SFTP (SSH File Transfer Protocol) are secure alternatives that provide encryption for file transfers.
Compatibility: FTP is supported by a wide range of operating systems and FTP clients, making it a versatile and widely used protocol for file transfer.
g) Hyper Text Transfer Protocol (HTTP)
HTTP (Hypertext Transfer Protocol) is a protocol used for transmitting hypertext documents (such as web pages) over the internet. It is the foundation of data communication for the World Wide Web.
Key features of HTTP include:
Client-Server Model: HTTP follows a client-server model, where a client (such as a web browser) sends a request to a server for a web resource, and the server responds with the requested resource.
Stateless Protocol: HTTP is stateless, meaning that each request from a client to a server is independent and not reliant on any previous requests. This allows for simple and efficient communication between clients and servers.
Request-Response Protocol: HTTP is based on a request-response protocol, where a client sends a request to the server, and the server responds with the requested resource (such as a web page or file).
Methods: HTTP defines several request methods, including GET (retrieve a resource), POST (submit data to be processed), PUT (upload a file to a server), and DELETE (delete a resource).
Headers: HTTP uses headers to provide additional information about a request or response. Headers can include information such as the content type, content length, and caching directives.
Status Codes: HTTP defines a set of status codes that indicate the outcome of a request. For example, a status code of 200 indicates a successful request, while a status code of 404 indicates that the requested resource was not found.
h) Hyper Text Transport Protocol Secure (HTTPS)
HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP that is used to secure the communication between a client and a server over the internet.
Key features of HTTPS include:
Encryption: HTTPS uses SSL/TLS (Secure Sockets Layer/Transport Layer Security) to encrypt the data transmitted between the client and server. This ensures that even if the data is intercepted, it cannot be read without the decryption key.
Authentication: HTTPS uses digital certificates to authenticate the identity of the server. This helps prevent man-in-the-middle attacks, where an attacker intercepts the communication between the client and server.

Data Integrity: HTTPS ensures that the data transmitted between the client and server has not been altered or tampered with during transmission. This is achieved through the use of cryptographic hash functions.
SEO Benefits: HTTPS is also important for SEO (Search Engine Optimization), as search engines like Google prioritize websites that use HTTPS over HTTP in their search rankings.
i) Terminal Emulation Protocol (Telnet)
Telnet is a network protocol used to establish a command-line connection to a remote device or server. It allows users to interact with the remote system as if they were directly connected to it, using a text-based interface.
Key features of Telnet include:
Remote Access: Telnet enables users to remotely access and manage devices, such as servers, routers, and switches, over a network.
Text-Based Interface: Telnet provides a text-based interface for interacting with the remote system, allowing users to execute commands and retrieve information.
Port 23: Telnet typically uses TCP port 23 for communication. When establishing a Telnet session, the client connects to the server's port 23 to initiate the connection.
Unencrypted Communication: By default, Telnet does not encrypt the data transmitted between the client and server, making it vulnerable to eavesdropping. For this reason, Telnet is considered insecure for transmitting sensitive information over the internet.
Replacement by SSH: Due to its lack of encryption, Telnet has largely been replaced by more secure protocols like SSH (Secure Shell), which encrypts data transmissions to protect against eavesdropping and unauthorized access.
While Telnet is still used in some environments where security is not a concern, it is generally recommended to use more secure protocols like SSH for remote access and management tasks.
j) Dynamic Host Configuration Protocol (DHCP)
DHCP (Dynamic Host Configuration Protocol) is a network management protocol used to dynamically assign IP addresses and other network configuration parameters to devices on a network. DHCP simplifies the process of configuring network settings for devices by automatically providing them with the necessary information.
Key features of DHCP include:
Automatic IP Address Assignment: DHCP automatically assigns IP addresses to devices when they connect to a network, eliminating the need for manual configuration of IP addresses.
IP Address Pooling: DHCP uses a pool of available IP addresses from which it assigns addresses to devices. This allows for efficient allocation of IP addresses and helps prevent address conflicts.
Lease Management: DHCP leases IP addresses to devices for a specific period of time, known as the lease duration. Devices can renew their leases before they expire, or DHCP can reclaim the addresses if they are no longer in use.
Configuration Parameters: In addition to IP addresses, DHCP can also provide devices with other network configuration parameters, such as subnet masks, default gateways, DNS (Domain Name System) servers, and domain names.
Centralized Management: DHCP allows for centralized management of IP address allocation and configuration, making it easier to maintain and administer large networks.
It is commonly used in home networks, corporate networks, and other environments where automated network configuration is required.
k) Address Resolution Protocol (ARP)
ARP (Address Resolution Protocol) is a protocol used to map an IP address to a MAC (Media Access Control) address in a local network. It is essential for communication between devices on the same subnet.
Here's how ARP works:
IP to MAC Address Resolution: When a device wants to communicate with another device on the same subnet, it needs to know the MAC address of the destination device. The device sends out an ARP request packet containing the IP address of the destination device.
ARP Request: The ARP request is broadcasted to all devices on the local network. The request asks the device with the matching IP address to respond with its MAC address.
ARP Reply: The device with the matching IP address responds with an ARP reply packet containing its MAC address.
Updating ARP Cache: Once the requesting device receives the ARP reply, it updates its ARP cache with the MAC address of the destination device. The ARP cache is a table that stores mappings of IP addresses to MAC addresses, which helps in future communication with the same device.
Subsequent Communication: With the MAC address of the destination device, the requesting device can now send data packets directly to the destination device using its MAC address.
ARP is a critical protocol for the functioning of Ethernet networks, as it enables devices to communicate with each other using their MAC addresses. It is a fundamental part of the TCP/IP protocol suite and is used in both IPv4 and IPv6 networks.
l) Secure Shell (SSH)
SSH (Secure Shell) is a network protocol that provides a secure way to access and manage remote devices or servers over an unsecured network. SSH uses encryption to ensure that data transmitted between the client and server is secure and protected from eavesdropping and tampering.
Key features of SSH include:
Secure Communication: SSH encrypts data transmitted between the client and server, preventing unauthorized access to sensitive information.
Authentication: SSH uses public-key cryptography to authenticate the client and server. This helps prevent man-in-the-middle attacks, where an attacker intercepts and modifies communication between the client and server.
Remote Access: SSH provides a secure way to remotely access and manage devices or servers. Users can log in to a remote system and execute commands as if they were physically present at the device.
File Transfer: SSH includes tools like SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol) for secure file transfer between devices.
Port Forwarding: SSH supports port forwarding, allowing users to securely access services running on a remote server as if they were running locally on their device.
(Port forwarding is a technique used in computer networking to allow a computer from outside your network to access a specific service or application on a computer within your network. It involves redirecting incoming network traffic from one port on your router to another port on a specific device in your local network.)
Tunneling: SSH can create encrypted tunnels between devices, allowing secure communication between two endpoints over an unsecured network.
Overall, SSH is a widely used protocol for secure remote access and management of devices and servers. It is commonly used by system administrators, developers, and anyone who needs to access remote systems securely.
m) Real Time Messaging Protocol (RTMP)
RTMP (Real-Time Messaging Protocol) is a protocol designed for streaming audio, video, and data over the internet in real-time. It was originally developed by Macromedia (now Adobe) for streaming audio, video, and data between a server and a Flash player.
Key features of RTMP include:
Low Latency: RTMP is designed for low-latency streaming, making it suitable for real-time applications such as live video streaming and online gaming.
Adaptive Bitrate Streaming: RTMP supports adaptive bitrate streaming, allowing the server to dynamically adjust the bitrate of the stream based on network conditions and client capabilities.
(Bitrate streaming, a technique used in streaming media over the internet to deliver the best possible playback experience to users with varying internet connection speeds. It works by dynamically adjusting the quality of the video or audio stream based on the available bandwidth and device capabilities.)
Secure Communication: RTMP can be used with SSL/TLS (Secure Sockets Layer/Transport Layer Security) to provide secure communication between the client and server.
Streaming Protocols: RTMP supports different streaming protocols, including RTMP, RTMPS (RTMP over SSL/TLS), RTMPE (RTMP encrypted), and RTMPT (RTMP tunneled over HTTP).
Support for Different Platforms: RTMP is supported on various platforms, including Adobe Flash Player, Adobe AIR, and some third-party players and servers.
While RTMP was widely used for streaming multimedia content in the past, it has been largely replaced by other streaming protocols such as HLS (HTTP Live Streaming) and DASH (Dynamic Adaptive Streaming over HTTP), which offer better compatibility and support for modern devices and browsers.
Transport Layer Deep Dive
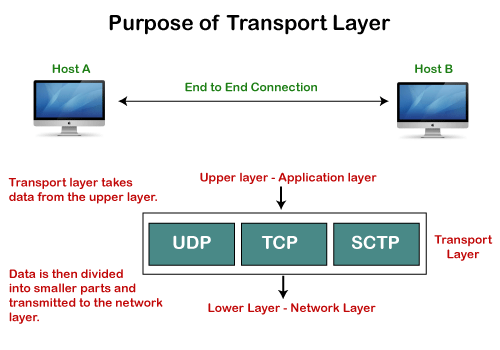
The IP layer gets packets from one node to another, but it is not well-suited to transport.
First, IP routing is a “best-effort” mechanism, which means packets can and do get lost sometimes.
Additionally, data that does arrive can arrive out of order.
Finally, IP only supports sending to a specific host; normally, one wants to send to a given application running on that host.
Email and web traffic, or two different web sessions, should not be commingled! The Transport layer is the layer above the IP layer that handles these sorts of issues, often by creating some sort of connection abstraction. Far and away the most popular mechanism in the Transport layer is the Transmission Control Protocol (TCP/IP) and User Datagram Protocol (UDP/IP).
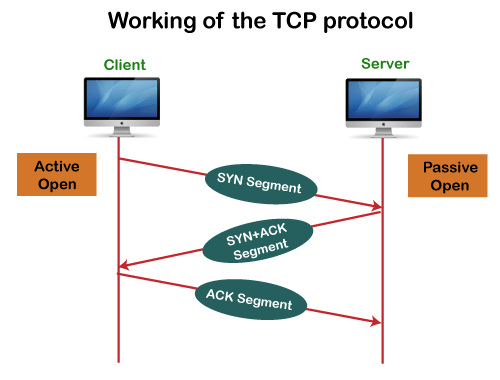
a) Transmission Control Protocol (TCP)
Transmission Control Protocol (TCP) is connection-oriented, meaning once a connection has been established, data can be transmitted in two directions. TCP has built-in systems to check for errors and to guarantee data will be delivered in the order it was sent, making it the perfect protocol for transferring information like still images, data files, and web pages. But while TCP is instinctively reliable, its feedback mechanisms also result in a larger overhead, translating to greater use of the available bandwidth on your network.
TCP Header Format
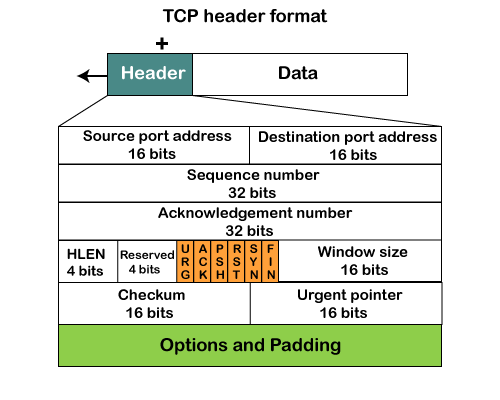
Source port: It defines the port of the application, which is sending the data. So, this field contains the source port address, which is 16 bits.
Destination port: It defines the port of the application on the receiving side. So, this field contains the destination port address, which is 16 bits.
Sequence number: This field contains the sequence number of data bytes in a particular session. Like a serial number for the data being sent. It helps the receiving end put the data packets back in the right order and detect if any packets are missing.
Acknowledgment number: When the ACK flag is set, then this contains the next sequence number of the data byte and works as an acknowledgment for the previous data received. For example, if the receiver receives the segment number 'x', then it responds 'x+1' as an acknowledgment number.
HLEN / Data offsets: It specifies the length of the header indicated by the 4-byte words in the header. The size of the header lies between 20 and 60 bytes. Therefore, the value of this field would lie between 5 and 15.
Reserved: It is a 4-bit field reserved for future use, and by default, all are set to zero.
Flags
There are six control bits or flags:URG: It represents an urgent pointer. If it is set, then the data is processed urgently.
ACK: If the ACK is set to 0, then it means that the data packet does not contain an acknowledgment.
PSH: If this field is set, then it requests the receiving device to push the data to the receiving application without buffering it.
RST: If it is set, then it requests to restart a connection.
SYN: It is used to establish a connection between the hosts.
FIN: It is used to release a connection, and no further data exchange will happen.
Window size
It is a 16-bit field. It contains the size of data that the receiver can accept. This field is used for the flow control between the sender and receiver and also determines the amount of buffer allocated by the receiver for a segment. The value of this field is determined by the receiver.Checksum
It is a 16-bit field. This field is optional in UDP, but in the case of TCP/IP, this field is mandatory.Urgent pointer
It is a pointer that points to the urgent data byte if the URG flag is set to 1. It defines a value that will be added to the sequence number to get the sequence number of the last urgent byte.Options
It provides additional options. The optional field is represented in 32-bits. If this field contains the data less than 32-bit, then padding is required to obtain the remaining bits.
b) User Datagram Protocol (UDP)
User Datagram Protocol (UDP) is a simpler, connectionless Internet protocol wherein error-checking and recovery services are not required. With UDP, there is no overhead for opening a connection, maintaining a connection, or terminating a connection; data is continuously sent to the recipient, whether or not they receive it.
Although UDP isn’t ideal for sending an email, viewing a web page, or downloading a file, it is largely preferred for real-time communications like broadcast or multitask network transmission.
UDP Header Format

TCP Vs UDP
IP Deep Dive
What is Internet Protocol (IP)?
The Internet Protocol (IP) is a protocol, or set of rules, for routing and addressing packets of data so that they can travel across networks and arrive at the correct destination.
Data traversing the Internet is divided into smaller pieces, called packets. IP information is attached to each packet, and this information helps routers to send packets to the right place.
Every device or domain that connects to the Internet is assigned an IP address, and as packets are directed to the IP address attached to them, data arrives where it is needed.
Once the packets arrive at their destination, they are handled differently depending on which transport protocol is used in combination with IP. The most common transport protocols are TCP and UDP.
What is an IP address and how does IP addressing work?
An IP address is a unique identifier assigned to a device or domain that connects to the Internet. Each IP address is a series of characters, such as '192.168.1.1'. Via DNS resolvers, which translate human-readable domain names into IP addresses, users are able to access websites without memorizing this complex series of characters.
Each IP packet will contain both the IP address of the device or domain sending the packet and the IP address of the intended recipient, much like how both the destination address and the return address are included on a piece of mail.
In Short: An IP address is a unique address that identifies a device on the internet or a local network. IP stands for "Internet Protocol," which is the set of rules governing the format of data sent via the internet or local network.
Important Notes
IP addresses are not random. They are mathematically produced and allocated by the Internet Assigned Numbers Authority (IANA), a division of the Internet Corporation for Assigned Names and Numbers (ICANN).
ICANN is a non-profit organization that was established in the United States in 1998 to help maintain the security of the internet and allow it to be usable by all.
Each time anyone registers a domain on the internet, they go through a domain name registrar, who pays a small fee to ICANN to register the domain.
What is an IP Packet?
An IP packet is a fundamental unit of data transmitted over an IP (Internet Protocol) network.
It consists of a header and a payload (data). The header contains information necessary for routing the packet from the source to the destination, while the payload contains the actual data being transmitted.
What is IP Version?
Packets that hold Internet Protocol data carry a 4-bit IP version number as the first field of its header.
Currently, only IPv4 and IPv6 packets are seen on the Internet, having IP version numbers 4 and 6, respectively.
As the version number is carried in a 4-bit field, only numbers 0-15 can be assigned, but only version 4 and 6 is active and getting used, others are either reserved or obsolete.
IPv4
IPv4 is an IP version widely used to identify devices on a network using an addressing system.
It was the first version of IP deployed for production in the ARPANET in 1983.
It uses a 32-bit address scheme to store 2^32 addresses which is more than 4 billion addresses.
It is considered the primary Internet Protocol and carries 94% of Internet traffic.
IPv6
IPv6 is the most recent version of the Internet Protocol.
This new IP address version is being deployed to fulfill the need for more Internet addresses.
It was aimed to resolve issues that are associated with IPv4. With 128-bit address space, it allows 340 undecillion unique address space.
IPv6 is also called IPng (Internet Protocol next generation).
Internet Engineer Task Force initiated it in early 1994. The design and development of that suite are now called IPv6.
IPv4 and IPv6
Types of IP Addresses
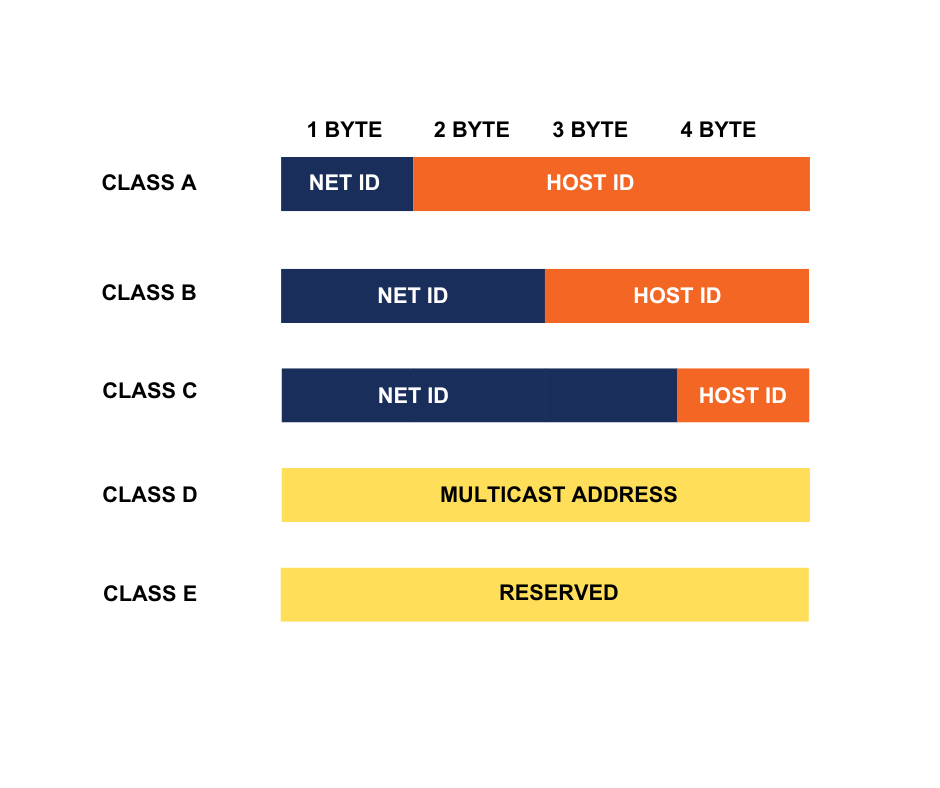
1) Based on Class
Early in the development of IP, the IANA (Internet Assigned Numbers Authority) designated five classes of IP address: A, B, C, D, and E.
a) Class A
In a Class A network, the first eight bits, or the first dotted decimal, is the network part of the address, with the remaining part of the address being the host part of the address.
There are 128 possible Class A networks. 0.0.0.0 to 127.0.0.0 The address 127.0.0.1 was reserved for the loopback (sometimes called "localhost") IP—this is the IP of the TCP/IP protocol itself on every host machine.
b) Class B
In a Class B network, the first 16 bits are the network part of the address.
All Class B networks have their first bit set to 1 and the second bit set to 0.
In dotted decimal notation, that makes 128.0.0.0 to 191.255.0.0 as Class B networks. There are 16,384 possible Class B networks.
c) Class C
In a Class C network, the first two bits are set to 1, and the third bit is set to 0. That makes the first 24 bits of the address the network address and the remainder as the host address.
Class C network addresses range from 192.0.0.0 to 223.255.255.0. There are over 2 million possible Class C networks.
d) Class D
These addresses are used for multicasting applications. Unlike the previous classes, the Class D is not used for "normal" networking operations. Class D addresses have their first three bits set to “1” and their fourth bit set to “0”.
Class D addresses are 32-bit network addresses, meaning that all the values within the range of 224.0.0.0 – 239.255.255.255 are used to uniquely identify multicast groups.
There are no host addresses within the Class D address space, since all the hosts within a group share the group’s IP address for receiver purposes.
d) Class E
Class E networks are defined by having the first four network address bits as 1. That encompasses addresses from 240.0.0.0 to 255.255.255.255.
Class E addresses were defined in the early days of the Internet but have not been used in practice. They are part of the original IP address space allocation scheme but are not allocated to any specific organization or use. As a result, Class E addresses are considered reserved and should not be used in public or private networks.
The exception is 255.255.255.255, which is used as a broadcast address.
Each class of address had a different default subnet mask and supported a different number of hosts per network, based on the remaining bits in the address. This addressing scheme has been largely superseded by Classless Inter-Domain Routing (CIDR), which allows for more flexible allocation of IP addresses and more efficient use of address space.

CIDR (Classless Inter Domain Routing)
CIDR (Classless Inter-Domain Routing) ranges are a way to specify IP addresses and their associated subnet masks in a flexible and efficient manner. CIDR notation is used to represent IP addresses and their subnet masks as a single string, using the format address/prefix-length.
Here's how CIDR ranges work:
Address: The address part of the CIDR range represents the network address or the base IP address.
Prefix Length: The prefix length indicates the number of bits in the subnet mask. It determines the size of the network and the number of hosts that can be assigned addresses within that network.
CIDR ranges allow for the efficient allocation of IP addresses by specifying the exact number of bits in the subnet mask, rather than relying on predefined address classes (A, B, C, etc.). This allows for more flexibility in designing and managing IP networks.
For example:
192.168.1.0/24represents the IPv4 address range from192.168.1.0to192.168.1.255, with a subnet mask of255.255.255.0.10.0.0.0/8represents the IPv4 address range from10.0.0.0to10.255.255.255, with a subnet mask of255.0.0.0.
CIDR ranges are commonly used in network configuration, routing, and IP address allocation to efficiently manage and allocate IP addresses in IPv4 and IPv6 networks.
2) Based on Accessibility
a) Private IP Addresses
- Private IP addresses are reserved addresses that are used within a private network to identify devices and communicate with them. These addresses are not routable on the public Internet, meaning they cannot be used to directly communicate with devices outside the private network. Private IP addresses are commonly used in home and business networks and are defined in RFC 1918.
b) Public IP Addresses
Public IP addresses are globally unique addresses assigned to devices connected to the Internet. These addresses are used for communication between devices across the Internet. Unlike private IP addresses, which are used within private networks, public IP addresses are routable on the Internet, allowing devices to communicate with each other across different networks.
Public IP addresses come in two forms – dynamic and static.
Dynamic IP addresses change automatically and regularly. ISPs buy a large pool of IP addresses and assign them automatically to their customers. Periodically, they re-assign them and put the older IP addresses back into the pool to be used for other customers.
In contrast to Dynamic IP addresses, static IP addresses remain consistent. Once the network assigns an IP address, it remains the same. Most individuals and businesses do not need a static IP address, but for businesses that plan to host their own server, it is crucial to have one. This is because a static IP address ensures that websites and email addresses tied to it will have a consistent IP address — vital if you want other devices to be able to find them consistently on the web.
c) Website IP Addresses
If you’re planning to start a website and you go with a web hosting service provider, you’ll potentially encounter two types of website IP address options: Shared IP Address and Dedicated IP Address.
- Shared IP Address: Used by multiple websites on the same server, sharing the same IP address. Each website has a unique domain name but shares the IP address. Example: www.smallbizstore.com (IP address: 192.168.1.1).

- Dedicated IP Address: Assigned exclusively to a single website, with the website having its own unique IP address. Example: www.largeecommercestore.com (IP address: 203.0.113.10).
Routers & Switches
What is Router?
A router is a networking device that forwards data packets between computer networks.
It operates at the network layer of the OSI model and uses routing tables to determine the best path for forwarding packets.
Routers are commonly used in homes, businesses, and the Internet to connect multiple networks together and enable communication between devices on different networks. They play a crucial role in directing traffic efficiently across networks and ensuring that data packets reach their intended destination.

What is Switch?
A network switch is a traffic director for your devices on a computer network. Unlike a hub, which simply broadcasts data to all devices, a switch reads the destination address of each data packet and intelligently sends it only to the intended recipient. This smarter method reduces congestion and improves overall network performance.
Switches operate at layer 2 of the OSI model, meaning they use media access control (MAC) addresses to make their decisions. They are essential components for any local area network (LAN) where multiple devices need to communicate efficiently.

Analogy for Router & Switch:
Imagine an office building. A switch is like a switchboard that connects all the phones within the office, allowing employees to call each other directly. A router is like the receptionist who directs incoming calls from outside the office to the correct employee's phone.
In short, a switch keeps traffic flowing smoothly within your network, while a router is the gatekeeper that controls traffic flow between your network and the outside world.
Routing Protocols
- Routing protocols are essential for efficient data transmission in computer networks. They determine the optimal path for data packets to travel from the source to the destination.
Here are some key routing protocols:
1) Interior Gateway Protocol (IGP)
Routing Information Protocol (RIP): A distance-vector protocol that uses hop count as a metric. RIP is simple to configure but has limitations in scalability and convergence time.
Open Shortest Path First (OSPF): A link-state protocol that uses the Dijkstra algorithm. It's more efficient than RIP, supports Variable Length Subnet Masking (VLSM), but is more complex to configure.
Interior Gateway Routing Protocol (IGRP): A Cisco proprietary protocol that uses bandwidth and delay as metrics. It's more advanced than RIP but lacks compatibility with other vendors.
2) Exterior Gateway Protocol (EGP)
- Border Gateway Protocol (BGP): An Exterior Gateway Protocol (EGP) used between routers in different autonomous systems. BGP is highly scalable and supports features like policy-based routing, but it's complex to configure.
3) Hybrid Routing Protocols
- Enhanced Interior Gateway Routing Protocol (EIGRP): A Cisco proprietary hybrid protocol that combines features of distance-vector and link-state protocols. EIGRP is efficient, scalable, and supports advanced features like unequal cost load balancing.
DNS (Domain Name System)
What is DNS?
The Domain Name System (DNS) is the phonebook of the Internet.
Humans access information online through domain names, like anytimes.com or espn.com. Web browsers interact through Internet Protocol (IP) addresses.
DNS translates domain names to IP addresses so browsers can load Internet resources. Each device connected to the Internet has a unique IP address which other machines use to find the device.
DNS servers eliminate the need for humans to memorize IP addresses such as 192.168.1.1 (in IPv4), or more complex newer alphanumeric IP addresses such as 2400:cb00:2048:1::c629:d7a2 (in IPv6).
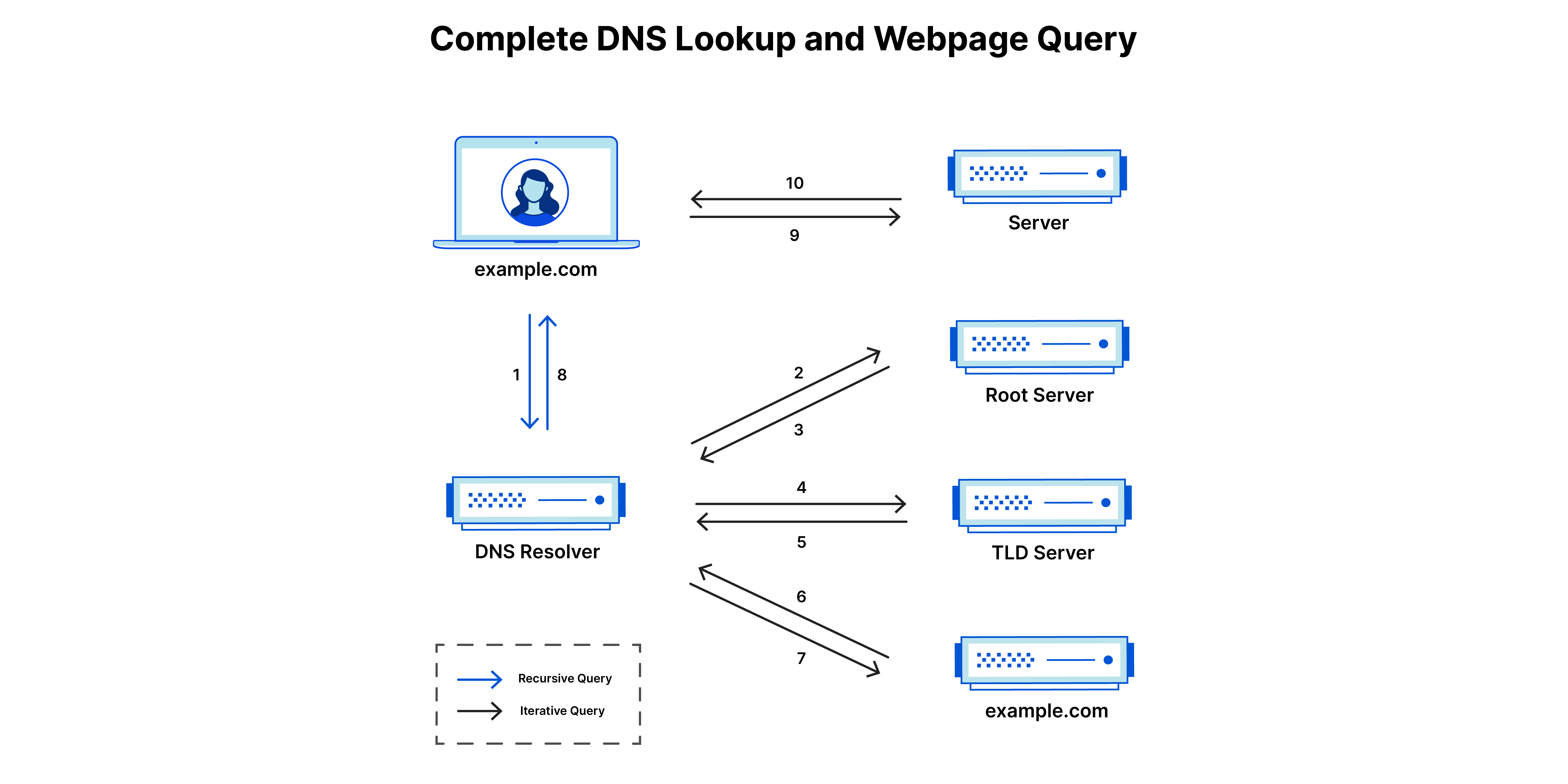
Steps in a DNS lookup & Retrieving Web Page / Content
- A user types ‘example.com’ into a web browser and the query travels into the Internet and is received by a DNS recursive resolver.
2. The resolver then queries a DNS root nameserver (.).
3. The root server then responds to the resolver with the address of a Top Level Domain (TLD) DNS server (such as .com or .net), which stores the information for its domains. When searching for example.com, our request is pointed toward the .com TLD.
4. The resolver then makes a request to the .com TLD.
5. The TLD server then responds with the IP address of the domain’s nameserver, example.com.
6. Lastly, the recursive resolver sends a query to the domain’s nameserver.
7. The IP address for example.com is then returned to the resolver from the nameserver.
8. The DNS resolver then responds to the web browser with the IP address of the domain requested initially.
9. Once the 8 steps of the DNS lookup have returned the IP address for example.com, the browser is able to make the request for the web page:The browser makes a HTTP request to the IP address.
10. The server at that IP returns the webpage to be rendered in the browser (step 10)
What is DNS record?
DNS records (aka zone files) are instructions that live in authoritative DNS servers and provide information about a domain including what IP address is associated with that domain and how to handle requests for that domain.
These records consist of a series of text files written in what is known as DNS syntax. DNS syntax is just a string of characters used as commands that tell the DNS server what to do.
All DNS records also have a ‘TTL’, which stands for time-to-live, and indicates how often a DNS server will refresh that record.
You can think of a set of DNS records like a business listing on Yelp. That listing will give you a bunch of useful information about a business such as their location, hours, services offered, etc.
Most common types of DNS record
a) (Address) A record - The record that holds the IP address of a domain.
b) (Canonical Name) CNAME record - Forwards one domain or subdomain to another domain, does NOT provide an IP address.
c) (Mail Exchange) MX record - Directs mail to an email server.
d) (Text) TXT record - Lets an admin store text notes in the record.
e) (Name Server) NS record - Stores the name server for a DNS entry.
f) (Start of Authority) SOA record - Stores admin information about a domain.
g) (Service Record) SRV record - Specifies a port for specific services.
h) (Pointer) PTR record - (Reverse of an A record) Provides a domain name in reverse-lookups.
Computer & Cloud Security
Computer Security
Computer security refers to the protection of computer systems and networks from unauthorized access, use, disclosure, disruption, modification, or destruction.
Effective computer security involves a combination of technical measures, such as firewalls and encryption, as well as policies and procedures, such as user education and incident response planning.
Types
a) Network security
- Protecting a computer network from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes implementing firewalls, intrusion detection systems, and virtual private networks (VPNs).
b) Endpoint security
- Protecting individual devices such as computers, laptops, and mobile devices from malware and other threats. This includes using antivirus software, firewalls, and other security software.
c) Application security
- Protecting software applications from attacks and vulnerabilities. This includes secure coding practices, code reviews, and penetration testing.
d) Data security
- Protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction. This includes data encryption, access controls, and secure backup and recovery.
e) Identity and access management
- Managing and controlling access to computer systems and networks by verifying the identities of users and devices. This includes user authentication and authorization techniques, such as passwords and tokens.
f) Disaster recovery and business continuity
- Planning for and responding to natural disasters, power outages, and other disruptions to ensure that critical systems and data can be restored quickly and efficiently.
Computer Security Threats
Different types of computer security threats briefly:
a) Malware: Malicious software that can infect a computer and cause harm, such as viruses, Trojan horses, worms, and ransomware.
b) Phishing: Attempts to trick users into providing sensitive information, such as passwords and credit card numbers, by disguising as a trustworthy entity in an electronic communication.
c) Social engineering: Using psychological manipulation techniques to trick users into providing sensitive information or performing actions that can compromise security.
d) Hacking: Attempts to gain unauthorized access to computer systems and networks, typically with the goal of stealing or modifying data.
e) Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks: Attempts to make a computer or network resource unavailable to its intended users by overwhelming it with traffic.
f) Advanced Persistent Threats (APTs): Long-term and targeted attacks, often carried out by nation-state actors or well-funded criminal organizations, with the goal of stealing sensitive information from the targeted organization.
g) Zero-day vulnerabilities: Unpatched software vulnerabilities that can be exploited by attackers before the vendor is even aware of the issue.
h) Insider threats: Security breaches caused by malicious or negligent employees or contractors with access to sensitive information.
i) IoT security: Inadequate security in Internet of Things (IoT) devices such as cameras, smart home devices, and medical equipment, which can be easily compromised and used to launch attacks on the network they are connected to.
k) Cryptojacking: Using someone else's computing resources to mine cryptocurrency without their knowledge or consent.
Cloud Security
Cloud security involves protecting data, applications, and infrastructure associated with cloud computing from various threats and unauthorized access.
It includes implementing measures and technologies to ensure the confidentiality, integrity, and availability of data and services in the cloud. This can include using encryption, access controls, and security best practices to mitigate risks and protect against cyberattacks.
Cloud Security Principles
Primary Measures
a) Access control: Controlling and monitoring who has access to cloud resources.
b) Data encryption: Protecting sensitive data both in transit and at rest.
c) Network security: Securing the communication channels used by the cloud service.
d) Incident response: Having a plan in place to respond to security breaches and other incidents.
e) Compliance: Adhering to industry regulations and standards such as SOC 2, PCI-DSS, and HIPAA.
f) Monitoring and logging: Keeping track of activity on the cloud service and being able to detect and investigate potential security incidents.
g) Regular security assessments and penetration testing: Identifying and mitigating vulnerabilities in the cloud environment.
Secondary Measures
a) Use virtual private clouds (VPCs) to create isolated networks within the cloud.
b) Use multi-factor authentication (MFA) to secure access to your cloud
resources.
c) Use security information and event management (SIEM) to monitor your cloud environment for security threats.
d) Use web application firewalls (WAFs) to protect your web applications from attacks.
e) Use intrusion detection and prevention systems (IDPS) to detect and block malicious traffic.
f) Use a VPN or Direct Connect to securely connect to your VPC.
Distributed Denial of Service (DDos)
DDoS (Distributed Denial of Service) is a type of cyber-attack that aims to make a network resource or a service unavailable to its intended users. This is accomplished by overwhelming the targeted website or network with a flood of traffic from multiple sources.
DDoS attacks are typically launched from a large number of compromised devices, such as computers, servers, and IoT devices, which are collectively referred to as a botnet. These devices are usually infected with malware that allows the attacker to remotely control them and use them to launch attacks.
There are several types of DDoS attacks, including:
a) Volume-based attacks
- Also known as volumetric attacks, these aim to overwhelm the target with a flood of traffic. They typically use protocols like UDP or ICMP to send a high volume of packets to the target. The goal is to consume all available bandwidth and resources, making the service unavailable to legitimate users. Mitigation strategies for these attacks often involve filtering out malicious traffic based on traffic patterns or using rate limiting to manage incoming traffic.
b) Protocol attacks
- These attacks exploit weaknesses in network protocols to exhaust server resources. For example, SYN flood attacks flood the target with TCP connection requests, but do not complete the handshake process, tying up resources. Similarly, fragmentation attacks send fragmented packets that are designed to consume resources when the target reassembles them. Protection against protocol attacks often involves implementing protocol-specific defenses, such as SYN cookies for SYN floods.
c) Application-layer attacks
- Also known as Layer 7 attacks, these target vulnerabilities in web applications themselves. For example, HTTP floods send a high volume of HTTP requests to a server, overwhelming it and causing it to become unavailable. Slowloris attacks are more subtle, sending HTTP headers to a server at a very slow rate to tie up resources. Defending against application-layer attacks often involves using web application firewalls (WAFs) to filter out malicious traffic and applying security patches to eliminate vulnerabilities in web applications.
DDoS attacks can have a significant impact on the availability and performance of a network or service, and can cause financial losses and reputational damage to the targeted organization. Therefore, it's important for organizations to implement DDoS protection measures such as using a DDoS protection service, setting up DDoS detection and mitigation tools, and having an incident response plan in place.
There are several ways to prevent Distributed Denial of Service (DDoS) attacks on web applications:
a) Use a DDoS protection service: Many cloud providers and third-party companies offer DDoS protection services that can filter out malicious traffic before it reaches the web application.
b) Implement rate limiting: Limit the number of requests a user or IP address can make to the web application in a given time period to prevent overwhelming the server with too many requests.
c) Use a Content Delivery Network (CDN): CDNs can help distribute traffic across multiple servers, making it more difficult for attackers to overload a single server with too much traffic.
d) Use a web application firewall (WAF): WAFs can help detect and block malicious traffic, such as traffic originating from known malicious IP addresses.
e) Use a Intrusion Detection and Prevention Systems (IDPS): IDPS can detect and block malicious traffic in real-time, and can also provide alerts when an attack is detected.
f) Have a DDoS response plan: Have a plan in place for responding to a DDoS attack, including identifying the attack, mitigating the attack, and restoring normal service.
g) Regularly test and monitor: Regularly test the web application's ability to withstand a DDoS attack and monitor the traffic to detect any unusual patterns or spikes.
It is important to note that no one method is foolproof and multiple layers of protection are usually required to effectively prevent a DDoS attack.
Firewall
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet.
The primary goal of a firewall is to block malicious traffic requests and data packets while allowing legitimate traffic through.

Firewalls come in various forms, but can be generally categorized by two main aspects:
Based on Deployment:
Network Firewall (Hardware Firewall): A physical device, often integrated into your router, that monitors and filters traffic entering and leaving your network.
Host-based Firewall (Software Firewall): A program installed on individual computers to regulate incoming and outgoing traffic specific to that device.
Based on Functionality (Inspection Method):
Packet-Filtering Firewall: Analyzes basic data packets like source/destination IP addresses and port numbers to allow or block traffic. (Simplest type)
Stateful Inspection Firewall: Tracks ongoing connections and filters traffic based on their established state, providing more granular control.
Application-Level Gateway (Proxy Firewall): Deeply inspects data at the application level, monitoring specific programs and protocols for security threats.
Some additional firewall types:
Next-Generation Firewall (NGFW): Combines traditional firewall features with advanced threat detection and prevention capabilities.
Cloud Firewall: Manages security for cloud-based applications and resources.
Some Useful Terms
Bandwidth: Bandwidth refers to the maximum rate of data transfer across a network path. It is often measured in bits per second (bps) and indicates the capacity of the communication channel.
Throughput: Throughput is the actual rate of successful data transfer over a network. It measures the amount of data transferred successfully in a given period and is often lower than the maximum bandwidth due to various factors like network congestion, errors, and protocol overhead.
Broadband: Broadband tells you how quickly data can be transferred, which is your overall measurement for the speed of your internet connection. This is significant for determining the speed at which your internet can perform certain tasks, such as streaming a movie.
Bit: Internet speed is measured in bits per second (bps). This is the smallest unit of computer information, so you’ll often see internet speeds referred to as megabits per second (Mbps)
Byte: 1 byte is equal to 8 bits. We use bytes to refer to how much memory is available or being transferred Mbps – “Megabits per second” is how we gauge internet speeds. This number represents the bandwidth of an internet connection, which is how much data can be transferred each second.
Mbps: “Megabits per second” is how we gauge internet speeds. This number represents the bandwidth of an internet connection, which is how much data can be transferred each second.
MBps: “Megabytes per second” measures the file size when talking about how much data can be transferred each second. You might also see this figure represented as MB.

- Latency: Latency measures the delay in data transfer between two points on a network.
Twisted Pair Cable
Ethernet Networks: Twisted pair cables, especially Unshielded Twisted Pair (UTP), are widely used for Ethernet networks in homes, offices, and data centers. They are used to connect computers, printers, routers, and other networking devices.
Telephone Lines: Twisted pair cables have been traditionally used for telephone lines, providing a simple and cost-effective way to transmit voice signals over short distances.

Co-axial Cable
Cable Television (CATV): Coaxial cables are commonly used to deliver cable television signals to homes and businesses. The shielding of coaxial cables helps prevent signal interference and ensures high-quality video transmission.
Broadband Internet: Coaxial cables are also used for broadband internet connections, particularly in cable modem systems. The high bandwidth capabilities of coaxial cables make them ideal for delivering high-speed internet access.

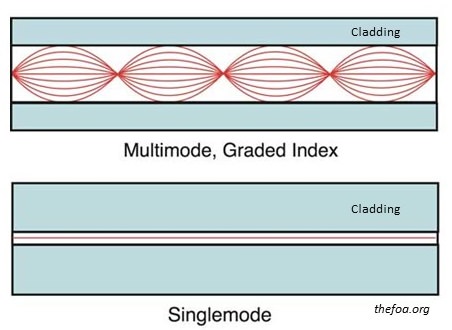
Optical Fiber Cable
Long-Distance Communication: Fiber optic cables are ideal for long-distance communication due to their ability to transmit data over long distances without signal degradation. They are used for telecommunications, internet backbone networks, and undersea cables.
High-Bandwidth Applications: Fiber optic cables are used in applications that require high bandwidth, such as data centers, cloud computing, and high-definition video streaming.
Secure Communication: Fiber optic cables are immune to electromagnetic interference, making them ideal for secure communication systems where data security is critical.